Abstract
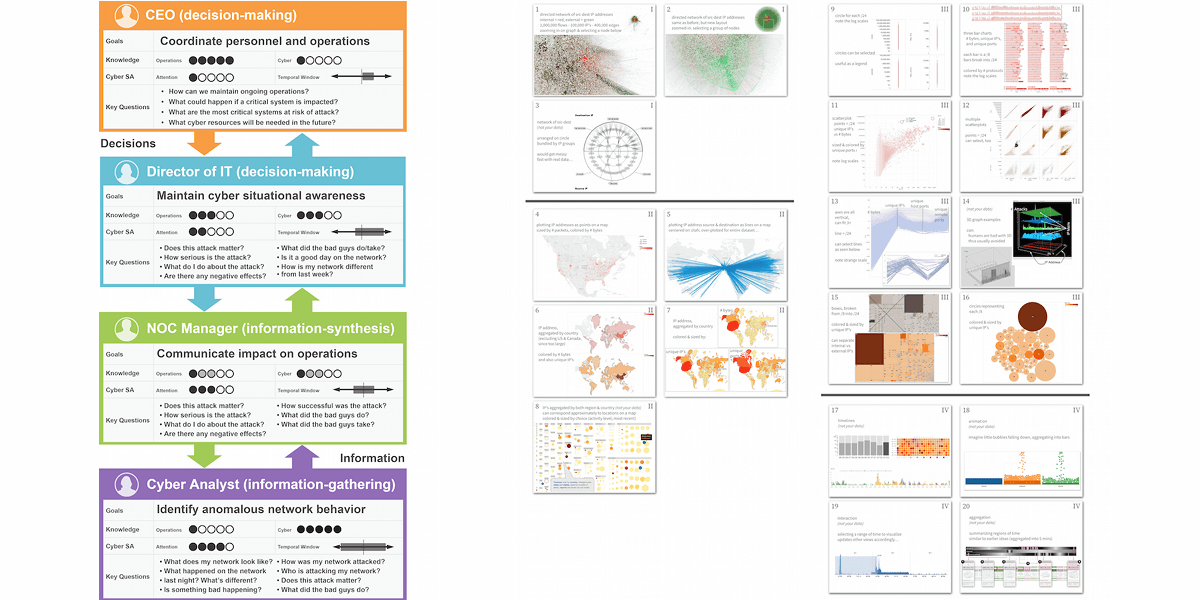
User-centered design can aid visualization designers to build better, more practical tools that meet the needs of cyber security users. The cyber security visualization research community can adopt a variety of design methods to more efficiently and effectively build tools. We demonstrate how previous cyber visualization research has omitted a discussion of effectiveness and process in the explanation of design methods. In this paper, we discuss three design methods and illustrate how each method informed two real-world cyber security visualization projects which resulted in successful deployments to users.
Citation
Sean McKenna,
Diane Staheli,
Miriah Meyer
Unlocking User-Centered Design Methods for Building Cyber Security Visualizations
Proceedings of the 12th International Symposium on Visualization for Cyber Security (VIS ’15), 2015.
BibTeX
@inproceedings{2015_vizsec_design-methods,
title = {Unlocking User-Centered Design Methods for Building Cyber Security Visualizations},
author = {Sean McKenna and Diane Staheli and Miriah Meyer},
booktitle = {Proceedings of the 12th International Symposium on Visualization for Cyber Security (VIS ’15)},
year = {2015}
}